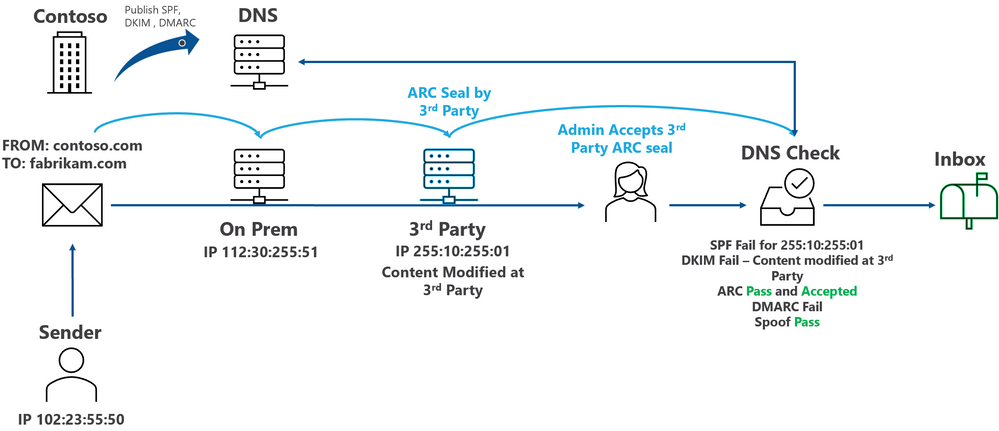
Back in October 2019, Microsoft included ARC support in their Microsoft 365 Roadmap, stating that “[ARC] is now enabled for Office 365 hosted mailboxes.” But at that time it could only be used between Office 365 tenants, or from Microsoft’s in-house services. However in June of 2022 they made it possible for each tenant to configure their own list of trusted third party ARC sealers.
An article on the Microsoft Defender for Office 365 Blog described ARC and how administrators were now able to define “trusted ARC sealers” in Microsoft 365 Defender. The result would be that when messages arrive from these trusted intermediaries – mailing lists, spam/malware filtering services, help desk operators – that have valid ARC Seals, but which fail DMARC and related email authentication checks, the results of the authentication checks the trusted intermediary performed and recorded in their ARC Seal could be used. “Trusted ARC sealers allows Microsoft to honor ARC signatures from these trusted intermediaries.”
In other words, it is possible for Office 365 tenants to configure trusted ARC Senders and eliminate one of the most frustrating interoperability issues people have when senders publish DMARC policies that block messages when they go through these intermediaries.
For details about configuring trusted ARC Senders in your Exchange 365 tenant, please refer to this article: Make a list of trusted ARC Senders to trust legitimate indirect mailflows